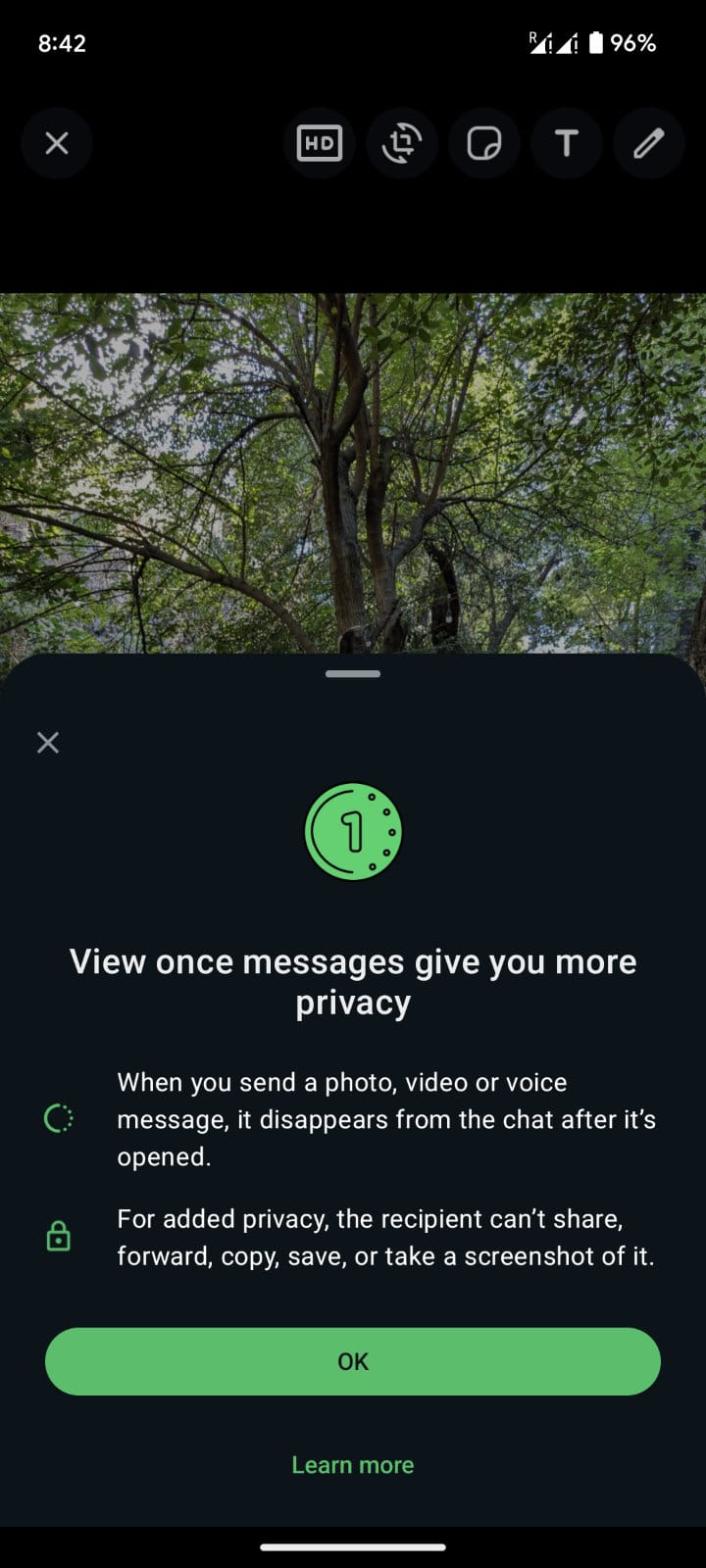
Researchers have uncovered a privacy flaw in WhatsApp’s “View Once” feature, designed to enhance user privacy by allowing media to be viewed once before disappearing. The flaw enables attackers to easily bypass this restriction, rendering the privacy protection mechanism ineffective while providing users with a false sense of protection.
While the ability to bypass WhatsApp’s View Once feature has been known for some time, with Chrome extensions offering this functionality, a report by the Zengo X Research team that thoroughly exposes the issue has brought renewed concern to the WhatsApp community.
The discovery was made during Zengo’s development of its new multi-party computation (MPC) crypto wallet interface, Zengo Desktop. In exploring similar mobile-first applications, the team examined WhatsApp’s privacy features, including “View Once,” and found that the feature’s implementation was deeply flawed, particularly when used on platforms like desktop and web, where WhatsApp does not offer full support for it.
Zengo’s investigation revealed the following flaws in View Once:
- Weak API controls: The “View Once” restriction is intended for mobile platforms, where WhatsApp can control actions like screenshots. However, the server API does not enforce these restrictions, allowing media to be downloaded on other platforms where these controls are not present.
- Simple flag manipulation: “View Once” messages are essentially regular media with a flag set to limit them to one view. By switching this flag from “true” to “false,” attackers can convert the message back into a regular media file that can be saved, forwarded, or shared.
- Unauthenticated downloads: Once the media URL is obtained, it can be downloaded from any device, as no authentication is required beyond the decryption key.
- Delayed deletion: Instead of being immediately removed from WhatsApp’s servers upon viewing, “View Once” media remains accessible for up to two weeks, providing attackers with an extended window to exploit the flaw.
Zengo reports that while building an unofficial WhatsApp client to demonstrate exploitation of the flaw, it discovered multiple cases of active exploitation in the wild, which is particularly concerning for a messenger platform used by over 2 billion people worldwide.

RestorePrivacy
Zengo suggests that WhatsApp can resolve the problem by implementing a more robust Digital Rights Management (DRM) system supported by hardware on modern operating systems like Android and iOS. A simpler, though less secure, approach would be to limit “View Once” media to mobile (primary) devices only and disable it on web and desktop platforms (companion apps).
WhatsApp’s response
WhatsApp, owned by Meta, acknowledged the issue to RestorePrivacy through a statement from spokesperson Zade Alsawah. They confirmed that updates to the “View Once” feature are being rolled out for web users, and they encouraged users to send sensitive media only to trusted contacts.
“Our bug bounty program is an important way we receive valuable feedback from external researchers and we are already in the process of rolling out updates to view once on web. We continue to encourage users to only send View Once messages to people they know and trust.”
WhatsApp spokesperson
WhatsApp also suggests that users read the Note section on the View Once’s FAQ page to better understand the feature’s practical limitations.
Whether or not the fixes will impact the functionality of the aforementioned Chrome extensions or unofficial client apps created to leverage the multiple flaws in the feature remains to be seen.
Until the flaws in View Once are validated by the security community as properly addressed, users should be cautious when relying on disappearing media features, especially when privacy is of utmost concern. Our recommendation is that users of any communication platform should never assume that disappearing message systems are foolproof.
Related: