The Tor Project is currently facing an unusual, ongoing attack aimed at its infrastructure. For several weeks, an unknown threat actor has been spoofing the IP addresses of Tor relays and directory authorities, sending fake TCP SYN packets over SSH’s port 22.
This technique has led to a flood of abuse complaints directed at Tor relay operators, even though their infrastructure is not involved in the actual traffic. In response to these complaints, hosting providers have temporarily suspended or restricted Tor servers, thus affecting some of the network’s capacity.
Attack overview and theories
Tor Project members initially flagged the attacks on a GitLab discussion. Operators like Pierre Bourdon also noticed unsolicited return traffic (RST and SYN-ACK packets) at very low rates on their relay machines, a pattern consistent with IP spoofing attacks. The Tor Project has been tracking this issue on GitLab and other forums, proposing several theories on the attack’s origin and purpose.
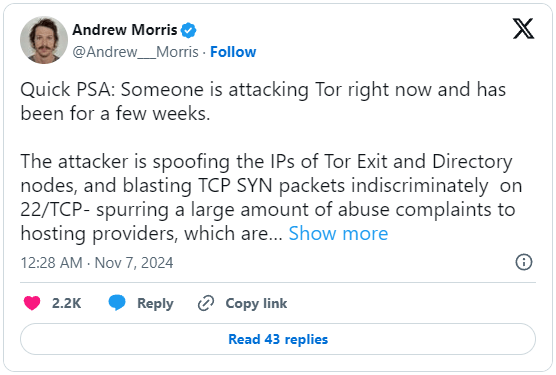

The leading hypothesis, according to Tor co-founder Roger Dingledine, is that attackers are spoofing Tor relay IPs to send SYN packets indiscriminately to SSH port 22 on other systems. This backscatter traffic prompts automated abuse complaints to hosting providers, causing them to take action against these IPs under the mistaken belief they are scanning for vulnerabilities. Another possibility, although less likely, is that compromised hosts are generating this backscatter traffic.
Impact on Tor operators
The sustained attack has led to frustration among Tor relay operators. Many reported receiving multiple abuse complaints from providers like Hetzner, IONOS, and OVH, resulting in service interruptions or server shutdowns. In some instances, operators’ accounts have been closed due to repeated complaints.
Tor Project’s response
In an official statement to RestorePrivacy, Pavel Zoneff, Director of Strategic Communications for the Tor Project, told us:
“The Tor Project is aware of recent spoofing attempts that have temporarily affected a small number of relays and is working to support any relay operators experiencing difficulties with their upstream providers as a result of this incident.
We want to reassure Tor users that this issue does not compromise the functionality or security of the Tor network. Affected operators are encouraged to reach out to us through our official support channels for guidance and assistance.” – Pavel Zoneff
Zoneff also urged the cybersecurity community to handle reports from watchdogcyberdefense.com with skepticism, as they have been a source of multiple abuse complaints, potentially stemming from false-positive or misleading reporting.
Mitigation efforts and recommendations
As the spoofing attacks continue, the Tor Project, with support from external analysts, has been working to trace the true origin of the spoofed packets and has reportedly identified and shut down at least one source of the disruptive traffic.
For relay operators and hosting providers, Tor suggests the following measures:
- IgHosting providers are advised to disregard abuse complaints, specifically citing port 22 scanning from known Tor node IPs.
- Tor operators are encouraged to monitor for SYN packet activity to help identify further attack patterns.
- Operators encountering issues should contact Tor Project support for guidance on dealing with abuse complaints and to report incidents.
In what concerns users of the Tor network, the project assured us that despite the disruptions, the Tor network remains fully functional and secure for end-users, so there’s no risk for their privacy and anonymity.